UltraVNC Backdoor via Dropbox
1. Executive Summary
This report documents a Windows endpoint compromise involving a trojanized UltraVNC installer delivered via a cloud-storage link (Dropbox). The analysis is performed exclusively against Sysmon telemetry captured in Microsoft-Windows-Sysmon-Operational.evtx.
Sysmon data shows that a user executed a suspicious binary from the Downloads folder. That binary:
- Originated from a Dropbox URL.
- Is widely detected as malicious under the hash
0cb44c4f8273750fa40497fca81e850f73927e70b13c8f80cdcfee9d1478e6f3. - Dropped additional artifacts to disk, including a script named
once.cmd. - Time-stomped a decoy PDF file to make it appear older and benign.
- Performed DNS lookups and outbound network connections to external infrastructure.
- Terminated after installing a backdoored UltraVNC remote-access component.
The activity aligns with public reporting from Palo Alto Networks Unit 42 on an UltraVNC-based backdoor distributed via Dropbox.
2. Scope and Evidence
2.1 Objectives
- Reconstruct the infection chain using Sysmon telemetry only.
- Identify initial access vector, execution behavior, filesystem artifacts, and network indicators.
- Determine likely impact and provide detection and hardening recommendations.
2.2 Evidence Base
Microsoft-Windows-Sysmon-Operational.evtx
- Loaded as a saved log in Windows Event Viewer.
- Key event IDs used:
- 1 – Process Create
- 2 – File Creation Time Changed
- 3 – Network Connection
- 5 – Process Terminated
- 11 – File Create
- 15 – FileCreateStreamHash (alternate data streams / Mark-of-the-Web)
- 22 – DNS Query
No disk image, memory capture, or network PCAP were available; all conclusions are derived from Sysmon plus external threat-intel lookups.
3. High-Level Timeline (UTC)
Exact timestamps are taken from Sysmon but omitted here for brevity; they can be recovered directly from the referenced event IDs in the original log.
- User downloads and executes malicious installer
- Sysmon Event ID 1 –
Preventivo24.02.14.exe.exestarted from the Downloads folder.
- Sysmon Event ID 1 –
- File creation and timestomping
- Event ID 11 – multiple new files written to disk (56 distinct file creation events overall).
- Event ID 2 – creation time on a decoy PDF is modified to an older timestamp.
- Mark-of-the-Web and distribution source confirmed
- Event ID 15 –
Zone.Identifierstream for the malicious binary shows Dropbox as the referrer.
- Event ID 15 –
- Dropped artifacts
- Event ID 11 – script file
once.cmdand additional components written under the user profile.
- Event ID 11 – script file
- Network activity
- Event ID 22 – DNS lookup to a benign-looking "connectivity-check" domain.
- Event ID 3 – outbound TCP connection from the malicious process to an external IP address (likely C2/remote-control infrastructure).
- Dropper self-termination
- Event ID 5 –
Preventivo24.02.14.exe.exeterminates after establishing the backdoor.
- Event ID 5 –
4. Detailed Analysis
4.1 Initial Access – User Execution of Malicious Installer
Evidence
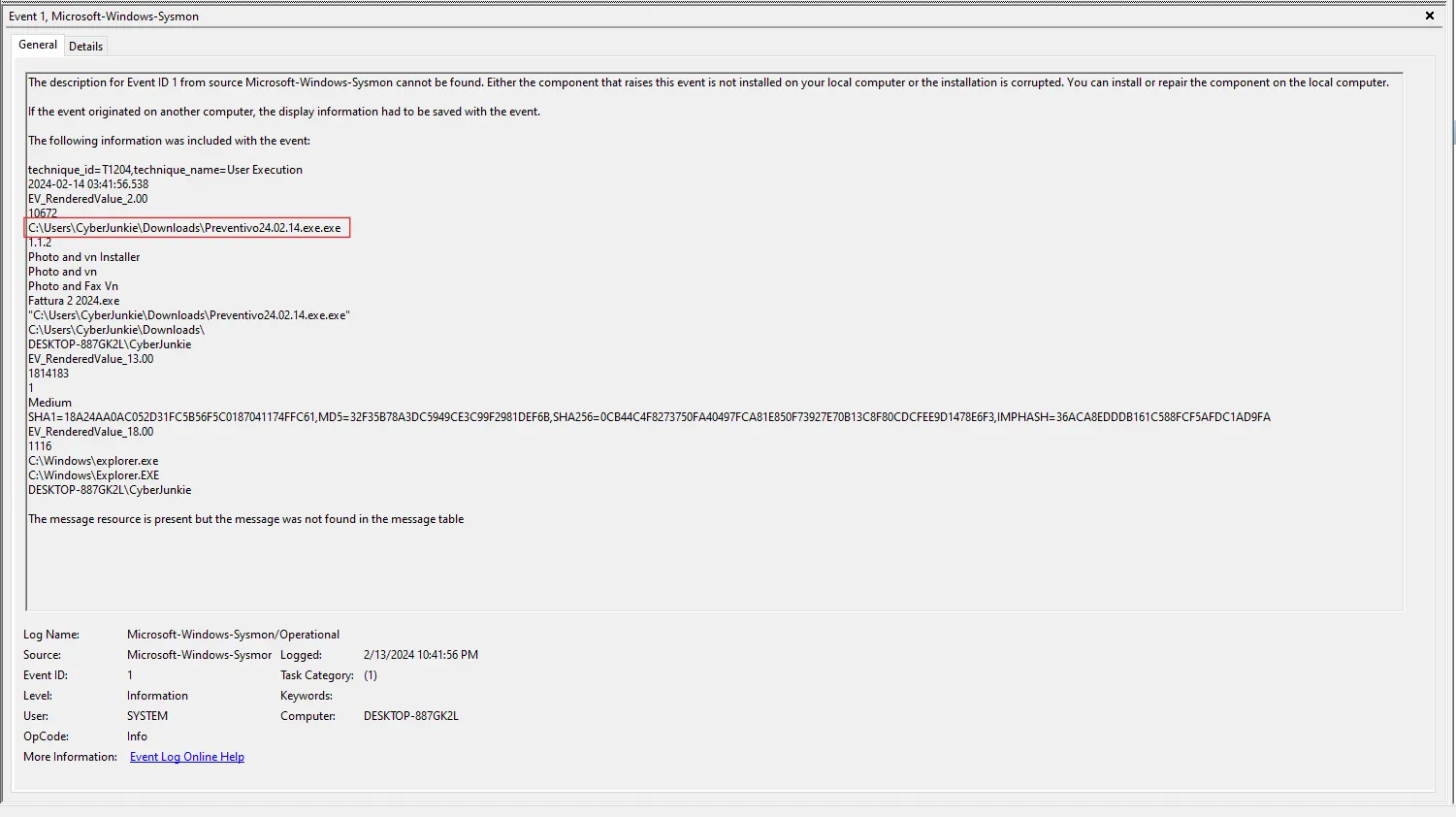
- Sysmon Event ID 1 entries filtered in Event Viewer.
- Suspicious process:
C:\Users\<victim>\Downloads\Preventivo24.02.14.exe.exe
Observations
- The binary name (
Preventivo24.02.14.exe.exe) is atypical and points to a potentially disguised executable (double extension). - Command-line, parent process and path are consistent with a user-initiated execution from the Downloads folder (e.g., via a web browser or file explorer).
- Sysmon provides multiple hash values (MD5/SHA1/SHA256). The SHA256 hash
0cb44c4f8273750fa40497fca81e850f73927e70b13c8f80cdcfee9d1478e6f3
was submitted to VirusTotal and flagged by numerous vendors as a malicious UltraVNC dropper / backdoor.
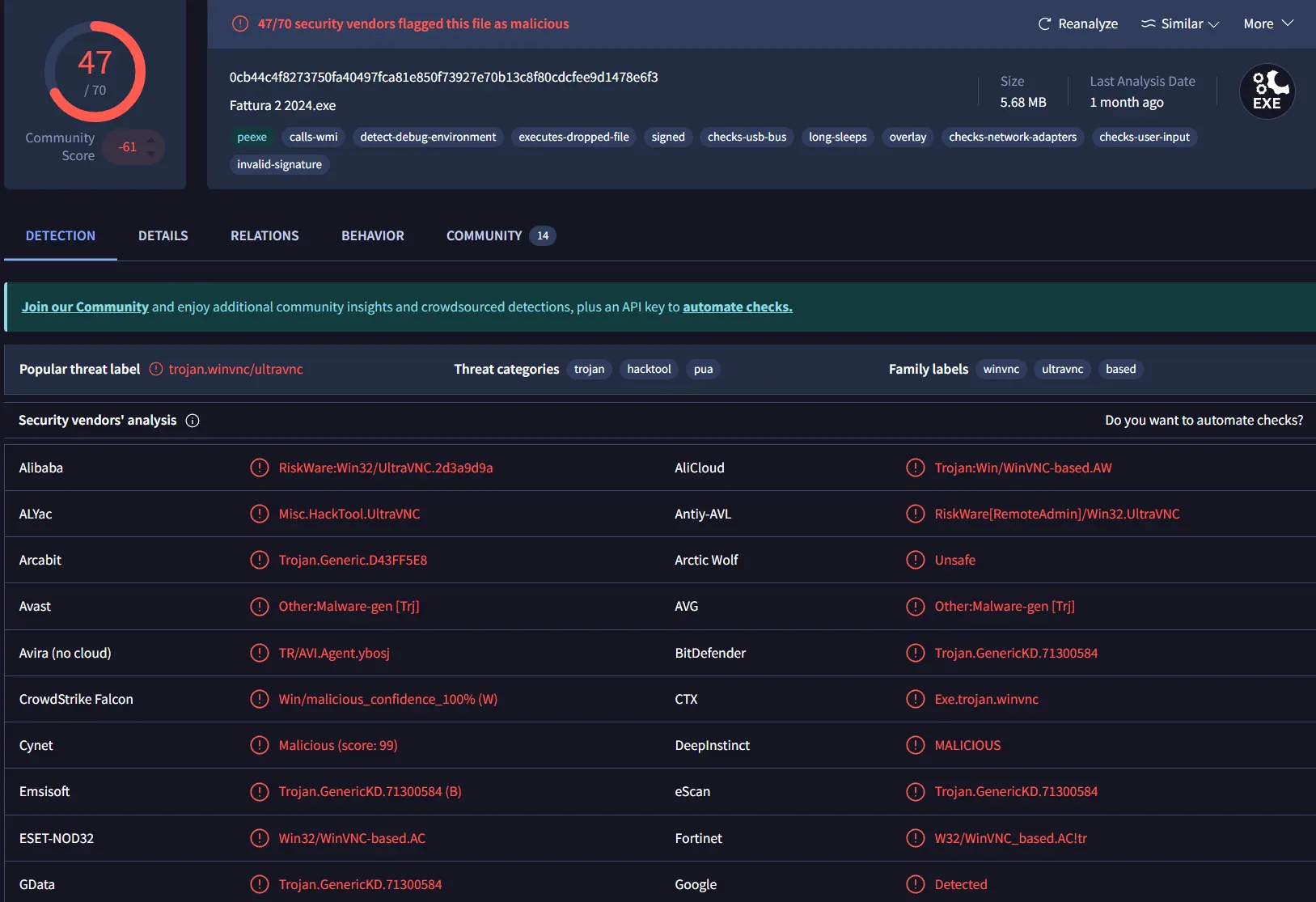
Assessment
The compromise begins with classic user execution (MITRE T1204) of a trojanized installer. There is no indication in Sysmon that exploitation of a software vulnerability was required; social engineering and a convincing filename were sufficient.
4.2 Distribution Vector – Dropbox Cloud Storage
Evidence
- Sysmon Event ID 15 – FileCreateStreamHash for the malicious binary.
- Alternate data stream:
Zone.Identifier.
Key Fields
ZoneTransferdata showing:ZoneIdindicating download from the Internet.ReferrerUrlcontaining a Dropbox URL.
Assessment
The malicious installer was delivered via Dropbox, which served as the initial hosting mechanism. This aligns with Unit 42's public reporting of trojanized UltraVNC installers being shared through cloud storage services.
From a blue-team perspective, this is an important pivot indicator: logs from web proxies, CASB, or cloud-app security tools should be used to identify similar outbound Dropbox access around the same time window.
4.3 File System Artifacts and Timestomping
4.3.1 File Creation Activity
Evidence
Sysmon filtered on Event ID 11 – FileCreate.
Observation
There are 56 file creation events recorded during the timeframe of interest. Several entries are associated with the Preventivo24.02.14.exe.exe process, including dropped executables, scripts, and supporting files.
This volume of file creation immediately after execution of an untrusted binary is consistent with an installer / dropper unpacking its payload.
4.3.2 Timestomping of Decoy PDF
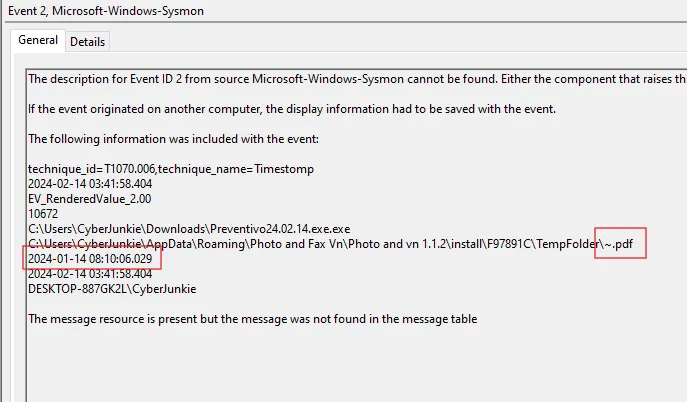
Evidence
- Sysmon Event ID 2 – File creation time changed.
- File path ending in
.pdfwith mismatched timestamps.
Observation
- The entry shows two separate timestamps:
- Original creation time.
- New creation time explicitly set by the malicious process.
- The new creation time is significantly older than the true execution time of the dropper.
- This is a classic timestomp technique (MITRE T1070.006 – "Indicator Removal on Host: Timestomp") used to:
- Make the PDF appear as if it predates the infection.
- Blend with legitimate documents so that simple "recent files" triage misses it.
Assessment
The decoy PDF likely served two purposes:
- Provide a social-engineering cover (opening a PDF to distract the user).
- Obfuscate incident-response timelines by falsifying creation metadata.
4.4 Dropped Script – once.cmd
Evidence
Sysmon Event ID 11 – FileCreate with TargetFilename ending in once.cmd.
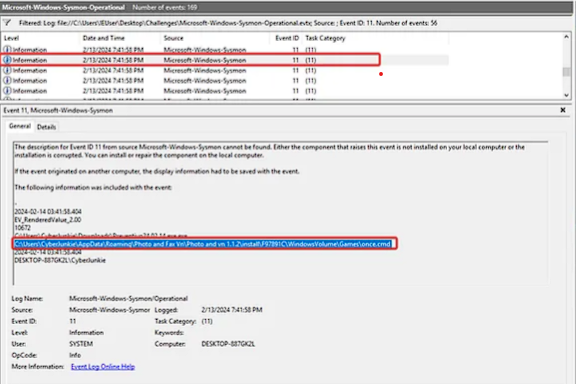
Observation
once.cmdis created shortly after the malicious EXE starts.- File path indicates it is written under the compromised user's profile or a related directory.
- Given typical UltraVNC backdoor behavior, this script is likely used to:
- Launch the backdoored UltraVNC binary,
- Configure persistence, or
- Perform one-time setup (registry keys, firewall rules, service installation).
Assessment
Even without content inspection of once.cmd, its mere existence tied to the malicious process should be treated as a high-fidelity indicator. In a production environment, this script would be a priority artifact to collect and reverse-engineer.
4.5 Network Activity and Command-and-Control
4.5.1 DNS Lookup – Connectivity Check
Evidence
- Sysmon Event ID 22 – DNS query.
- Query performed by the malicious process.
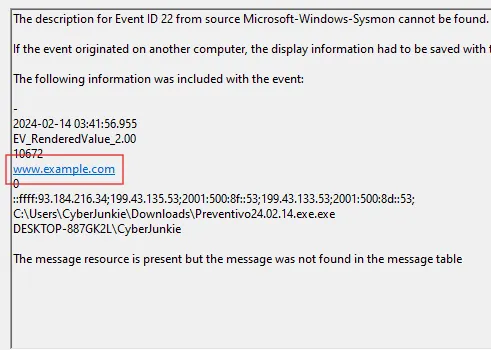
Observation
- The dropper performs a DNS lookup to a single, benign-looking "dummy" domain.
- This behavior is consistent with connectivity checks: malware verifying that the host has Internet access before contacting C2.
Assessment
While the specific FQDN is not repeated here, it should be treated as an indicator of compromise in the context of this campaign. In enterprise telemetry, a sequence of:
- Execution of an unknown binary from Downloads, followed by
- Immediate DNS query to this domain
would be a strong detection candidate.
4.5.2 Outbound Connection – UltraVNC C2
Evidence
Sysmon Event ID 3 – Network connection.
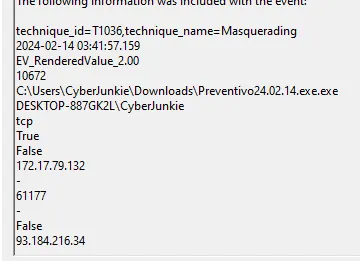
Observation
- The malicious process opens a TCP connection to a single external IP.
- Sysmon records the:
SourceImage(Preventivo24.02.14.exe.exe),SourceIp(local host),DestinationIp(remote infrastructure),DestinationPort(consistent with remote-access / VNC usage).
Assessment
This event likely represents the initial beacon or remote-access setup for the UltraVNC backdoor. Correlation with firewall or proxy logs would allow this IP to be confirmed and blocked across the environment.
4.6 Dropper Self-Termination
Evidence
Sysmon Event ID 5 – Process terminated for Preventivo24.02.14.exe.exe.
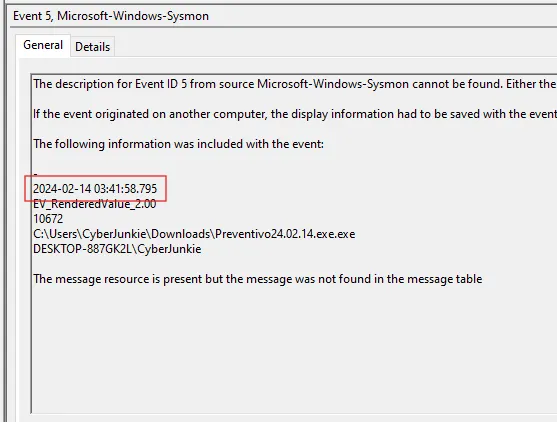
Observation
- After writing files, timestomping, and establishing network connectivity, the originating process cleanly terminates.
- This is typical behavior for a stager that:
- Installs its payload (backdoored UltraVNC),
- Hands off persistence and C2 duties to another binary/service, and
- Exits to reduce its forensic footprint.
Assessment
At the end of this chain, the host remains compromised via the installed UltraVNC component, even though the original EXE is no longer running. Any response plan must therefore focus not only on the dropper but also on the installed remote-access tooling and associated configuration.
5. Indicators of Compromise (IOCs)
Values marked "from Sysmon" can be recovered directly from the original log file and correlated with enterprise telemetry.
5.1 Files and Hashes
- Malicious Dropper
- Path:
C:\Users\<victim>\Downloads\Preventivo24.02.14.exe.exe - SHA256:
0cb44c4f8273750fa40497fca81e850f73927e70b13c8f80cdcfee9d1478e6f3 - Behavior: trojanized UltraVNC installer / backdoor.
- Path:
- Decoy PDF
- Path: PDF dropped under the victim user's profile (see Sysmon Event ID 2 and 11).
- Characteristics: creation time altered to an older date via timestomping.
- Script
- File:
once.cmd - Path: created under the victim profile (Sysmon Event ID 11).
- Likely role: one-time setup and/or launcher for UltraVNC payload.
- File:
5.2 Network
- Distribution
- Referrer: Dropbox URL associated with the malicious EXE download (Sysmon Event ID 15 –
Zone.Identifierstream).
- Referrer: Dropbox URL associated with the malicious EXE download (Sysmon Event ID 15 –
- Connectivity Check
- DNS: Single "dummy" domain used to verify outbound connectivity (Sysmon Event ID 22).
- Command-and-Control
- Destination IP: External address contacted by the malicious process (Sysmon Event ID 3).
- Protocol: TCP (port consistent with remote access / VNC usage).
5.3 Sysmon Patterns
- 56 FileCreate events in a short window following execution of the dropper.
- File creation-time changes (Event ID 2) targeting a PDF file.
- Process tree originating from
Preventivo24.02.14.exe.exefollowed by:- DNS (Event ID 22),
- Network connections (Event ID 3),
- Termination (Event ID 5).
6. Impact Assessment
If this activity were observed in a production environment, the likely impact would include:
Potential Impact
- Unauthorized remote access to the workstation via a backdoored UltraVNC instance.
- Opportunity for attackers to:
- Steal credentials (keylogging, LSASS dumping via remote session),
- Exfiltrate sensitive documents,
- Install additional tooling (lateral-movement frameworks, ransomware, etc.).
- Potential for the compromised host to be used as a pivot point deeper into the environment.
Because the dropper terminates after installation, standard process-based monitoring may miss the ongoing compromise unless the UltraVNC component itself is detected.
7. Detection and Hardening Recommendations
7.1 Endpoint Telemetry and Detection Engineering
- Detect execution of binaries from user Downloads/Temp paths
- Alert on unknown executables launched from:
C:\Users\*\Downloads\C:\Users\*\AppData\Local\Temp\
- Correlate with Event ID 1 + new file writes (Event ID 11).
- Alert on unknown executables launched from:
- Monitor for Sysmon Event ID 2 (Timestomp)
- Alert when creation times are changed on:
- User-accessible documents (
*.pdf,*.docx,*.xlsx), - Executable content (
*.exe,*.dll).
- User-accessible documents (
- Combine with process context (non-system binaries modifying timestamps).
- Alert when creation times are changed on:
- Script Drop Detection
- Flag creation or modification of
*.cmd,*.bat,*.ps1adjacent to newly executed binaries, especially under user profiles.
- Flag creation or modification of
- UltraVNC / Remote-Access Tooling
- Maintain allow-/deny-lists for remote-access tools in the environment.
- Alert on unexpected UltraVNC binaries, services, or listening ports.
7.2 Network Controls
- Cloud Storage Monitoring
- Log and monitor outbound access to file-sharing platforms (Dropbox, etc.).
- Flag downloads of executables from those domains.
- DNS-based Detections
- Watch for rare or campaign-specific "connectivity check" hostnames.
- Combine with preceding execution of unsigned binaries to form high-confidence alerts.
- Outbound Connection Filtering
- Restrict or closely monitor outbound ports commonly abused by RATs/VNC.
- Block known malicious IPs once identified from Sysmon or threat-intel feeds.
7.3 User Training and Policy
- Security Awareness
- Educate users on the risks of executing unsigned or unexpected installers received via email, chat, or cloud-storage links.
- Application Control
- Implement allow-listing (e.g., AppLocker, WDAC) where feasible to limit execution of arbitrary EXEs from user-writable directories.